SOC processes and best practices
One of the most valuable tools an airline pilot has at his disposal is the simplest one. A checklist. The checklist enumerates every single thing that must be done in order to maintain safety, avoid risk, and protect valuable lives. This ensures that you can get to your final destination without spilling any peanuts.
![]() The cyber security world isn’t all that different, yet the stakes are even higher.
The cyber security world isn’t all that different, yet the stakes are even higher.
There is a long list of things that the SOC team needs to do—and do properly—so that your organization’s assets are protected and high priority threats are detected quickly and with minimal impact.
In this chapter, we’ll help you establish the key processes and best practices that your SOC team will need to perform to detect emerging threats; determine their scope and impact; and respond effectively and quickly. At every step along the way, we’ll show you how you can use AlienVault® Unified Security Management® (USM), AlienVault Open Threat Exchange® (OTX™), and AlienVault Labs Threat Intelligence to power your SOC process.
Key Takeaways
Establish the key processes you’ll need for building a SOC. These include Event Classification & Triage; Prioritization & Analysis; Remediation & Recovery; and Assessment & Audit. Measure progress based on pragmatic SOC metrics. Examine how AlienVault USM supports these critical processes.

Answering the Big Questions
for Each SOC Stage
Stage One: Event Classification & Triage
How to Staff Your Team
| Alarm Types | Description | Priority Level | Tier 1 Analyst Tasks |
|---|---|---|---|
|
Alarm Types
Reconnaissance & Probing |
Description
Behavior indicating an actor attempting to discover information about the organization |
Priority Level

Low
|
Tier 1 Analyst Tasks
Review activity from OTX (on a weekly basis) |
|
Alarm Types
Delivery & Attack |
Description
Behavior indicating an attempted delivery of an exploit |
Priority Level

Low/Med
|
Tier 1 Analyst Tasks
Review activity from OTX (on a weekly basis) |
|
Alarm Types
Exploitation & Installation |
Description
Behavior indicating a successful exploit of a vulnerability or backdoor /RAT being installed on a system |
Priority Level

Med/High
|
Tier 1 Analyst Tasks
Verify and investigate (escalate to Tier 2) |
|
Alarm Types
System Compromise |
Description
Behavior indicating a compromised system |
Priority Level

High
|
Tier 1 Analyst Tasks
Verify and Investigate (escalate to Tier 2) |
Document All the Things

As a SOC analyst, it’s essential to document every stage of an investigation: which assets you’ve examined, which ones have “special” configuration or are owned by VIPs (aka execs), and which events are false positives. AlienVault USM makes this part of the process super easy. From any alarm, event, or vulnerability that AlienVault USM detects within your environments, you can easily open and track tickets with third-party productivity tools like ServiceNow and Jira, without leaving the USM platform. You can also use labels within AlienVault USM to classify, track, and search vulnerabilities and alarms. Documenting the investigation provides an audit trail in case it’s targeted again or is involved in future suspicious activity. Even if your company is not subject to an audit now, having this valuable information may prove useful in the future.
Stage Two: Prioritization & Analysis
Know All Your Environments and Assets
Asset discovery and inventory is one of the most important and yet most overlooked cybersecurity capabilities When you’re on the SOC team, having access to an updated and automated asset inventory is invaluable. AlienVault USM continuously scans your cloud and on-premises environments to discover assets to monitor. On- premises, you can discover all the IP-enabled devices on your network, as well as identify what software and services are running on them, and whether they include potential vulnerabilities. For your AWS and Azure cloud infrastructure, AlienVault USM provides visibility into the assets in your dynamically changing environments.
- What systems are critical to the ongoing function of your company?
- Which systems are critical to the day-to-day tasks?
- What other systems, devices, or networks do those critical assets and services rely on?
- Which systems manage and store sensitive information?
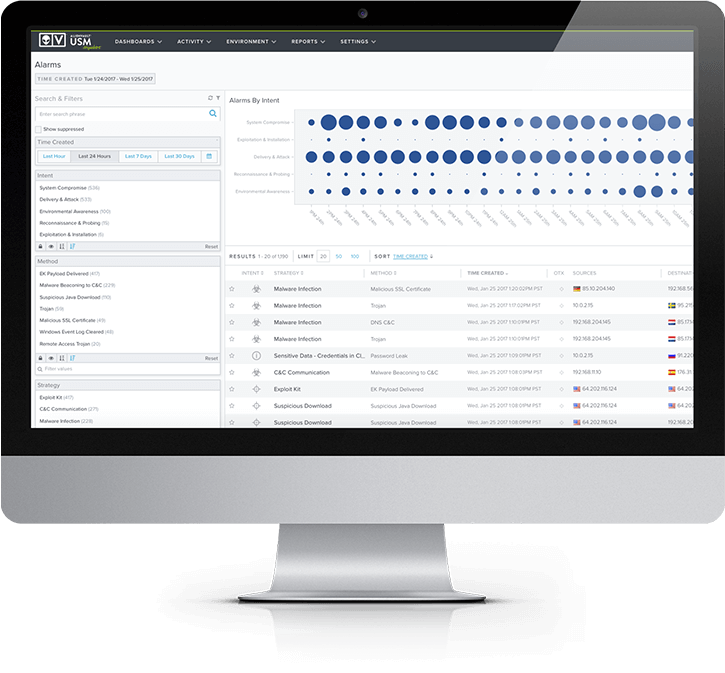
Learn more about AlienVault USM asset discovery capabilities ›