How to build a SOC: threat intelligence
The Recipe for Threat Intelligence = Context + Attribution + Action
Monitoring your environment for nefarious activity assumes that you know what those nefarious folks are doing, what “it” looks like, and how to find this activity across your critical infrastructure in the cloud and on-premises. The “bread crumbs” that these adversaries leave are usually of the same sort: IP addresses, host and domain names, email addresses, filenames, and file hashes.
With this amount of information, you can’t actually get that far. As a SOC analyst conducting an in-depth investigation, you need to be able to attribute these bread crumbs to specific adversaries, understand their methods, know their tools, recognize their infrastructure, and then build countermeasures for preventing attacks from them.
Some may refer to these “bread crumbs” or indicators (IOCs = indicators of compromise) as threat intelligence. This is far from the truth. On their own, without any context, they exist only as artifacts or clues. They can be used to begin an investigation but they rely on context, attribution, and action to become the high-quality threat intelligence that is essential for building a SOC.
Key Takeaways
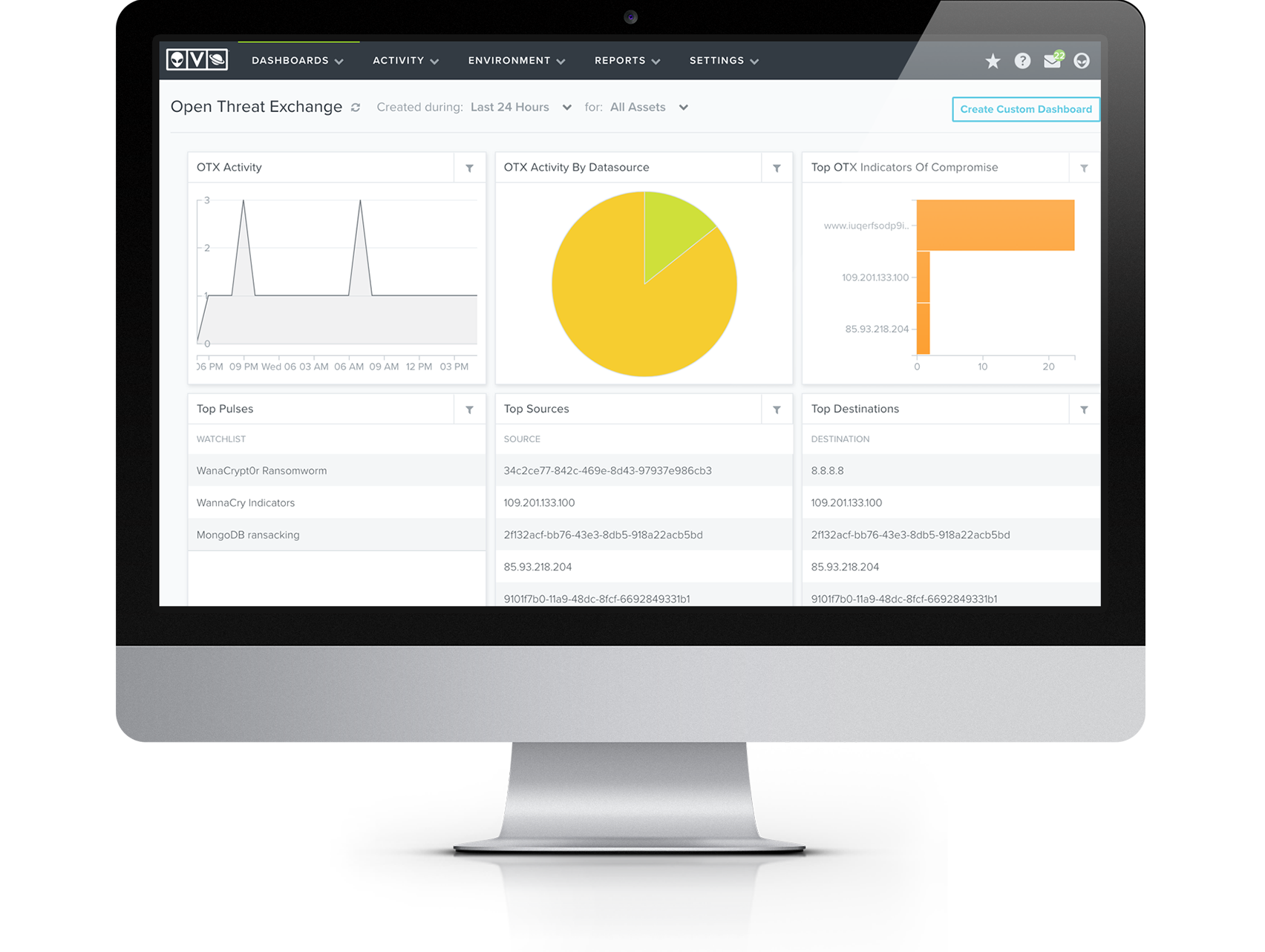
Understand the differences among tactical, strategic & operational intelligence and the specific ways these are used when building a SOC. Examine the benefits of combining crowd-sourced and proprietary data sources and explore key aspects of AlienVault Open Threat Exchange® (OTX™) and the AlienVault Labs Security Research Team.

“Know thyself. Know thy enemy. A thousand battles. A thousand victories.”
— Sun Tzu, The Art of War
Context
It’s a cliché, but it’s true. Context is king. An indicator without the necessary context doesn’t tell you much, but with it, you’ll have an idea of its urgency, relevance, and relative priority. Answering these sorts of questions can get questions can get you closer to achieving the necessary context, once you have an indicator which may signal a potential threat:
- What role does this indicator (or activity) play in an overall threat?
- Does its presence signify the beginning of an attack (reconnaissance and probing vs. delivery and attack)? Or a system compromise? Or data leakage?
- Is this threat actor known for this type of behavior?
- Is there significance in the asset that’s been targeted?
- How sophisticated is this particular indicator (e.g. malware sample)?
- What are the motivations of the threat actor behind this activity?
- What are the other activities that occurred on the same asset before and after this one?
- What about my other assets now or in the past?
Attribution
Knowing who is behind an attack is an essential part of knowing how to respond, including understanding the full scope of an attack, as well as the key tactics to take in response. It’s very similar to how the FBI uses profiles to track down suspects. Intent and motivation are the principal factors in analyzing criminal behavior, and the same applies within the cyber security realm. It’s easy to get caught up in the technical aspects of a particular attack, and how an exploit might work. But don’t forget, these tools have a human face behind them, driven by either profit or other ill intent. And knowing these details will give you leverage in terms of uncovering their work as well as how to build better countermeasures.

Action
Knowing something is only valuable if you can do something with what you know. By its very nature, the value of threat intelligence is ephemeral. The details of an attack that you may discover today may not retain their value in one week, or one month. Because, as we know, the world is constantly changing. Attacker’s are constantly changing too. They change their methods, their tools, and their infrastructure. That’s why it’s essential to act on what you discover as quickly as possible, while it remains current, true, and reflective of the current risks at hand. In fact, if you cannot implement the intelligence that you’re currently collecting in terms of improved monitoring, active defense, and better decision-making, you might as well not have the intelligence at all.

With these three elements in place—context, attribution, and action—threat intelligence can accomplish its essential goals: assist the SOC team with making the right decisions when it comes to preventing an attack as well as decreasing the time it takes to discover one in action. It can also help the SOC team establish the urgency they need to gain executive attention and sponsorship.
3 Types of Threat Intelligence for SOC Teams
The following table outlines how each of the three types of threat intelligence—tactical, strategic, and operational—offer context, attribution, and action and enable a solid foundation for building a SOC.
|
TACTICAL
Offers clues (without context and attribution)
|
STRATEGIC
Provides context and attribution to inform action
|
OPERATIONAL
Applies context and attribution to enable action
|
|
|---|---|---|---|
|
Description |
TACTICAL
Indicators, artifacts, and other evidence (e.g. IOCs) about an existing or emerging threat to assets. |
STRATEGIC
“Big picture” analysis of adversary TTPs (tools, tactics, and procedures) conducted by security experts to arm and inform SOC teams in building an effective cybersecurity strategy. |
OPERATIONAL
Updated signatures, rules, and other defensive countermeasures that “arm and inform” your monitoring infrastructure based on collecting and analyzing the latest raw indicators and other artifacts. |
|
Use Case |
TACTICAL
SOC analysts use these artifacts to detect emerging risks and share information about them with others to improve security for all. |
STRATEGIC
SOC analysts and SOC leaders review to better understand adversary motivations and tradecraft, make more informed business decisions, and ensure alignment between their cybersecurity strategy and real world risk. |
OPERATIONAL
SOC analysts get notified of the latest threats in their environment based on automated updates to their SIEMs, IDS, vulnerability scanners, and other SOC tools. |
|
How it |
TACTICAL
AlienVault Unified Security Management® (USM) receives continuous updates with the latest indicators from the AlienVault Labs Security Research Team. These updates leverage threat data from the larger community in AlienVault OTX, so they reflect in-the-wild attacks on organizations of all sizes from around the world. |
STRATEGIC
AlienVault Labs Security Research Team members spend countless hours researching the latest threat actors and their methods. These discoveries are integrated into the USM platform through continuous threat intelligence updates, which include rich, context-specific guidance on how to respond to threats detected in your environments. |
OPERATIONAL
The AlienVault Labs Security Research Team regularly publishes threat intelligence updates to the USM platform in the form of correlation directives, IDS signatures, vulnerability audits, asset discovery signatures, IP reputation data, data source plugins, and report templates. The Security Research Team also leverages the power of AlienVault OTX, the world’s largest crowd- sourced repository of threat data to provide global insight into attack trends and bad actors. |
|
Key Benefits |
TACTICAL
|
STRATEGIC
|
OPERATIONAL
|
Threat Intelligence Approaches
There are a few options for sourcing threat intelligence that will feed your SOC, and it’s helpful to understand what each brings to the table. Keep in mind that AlienVault has incorporated each one of these approaches into the USM platform.


.png)